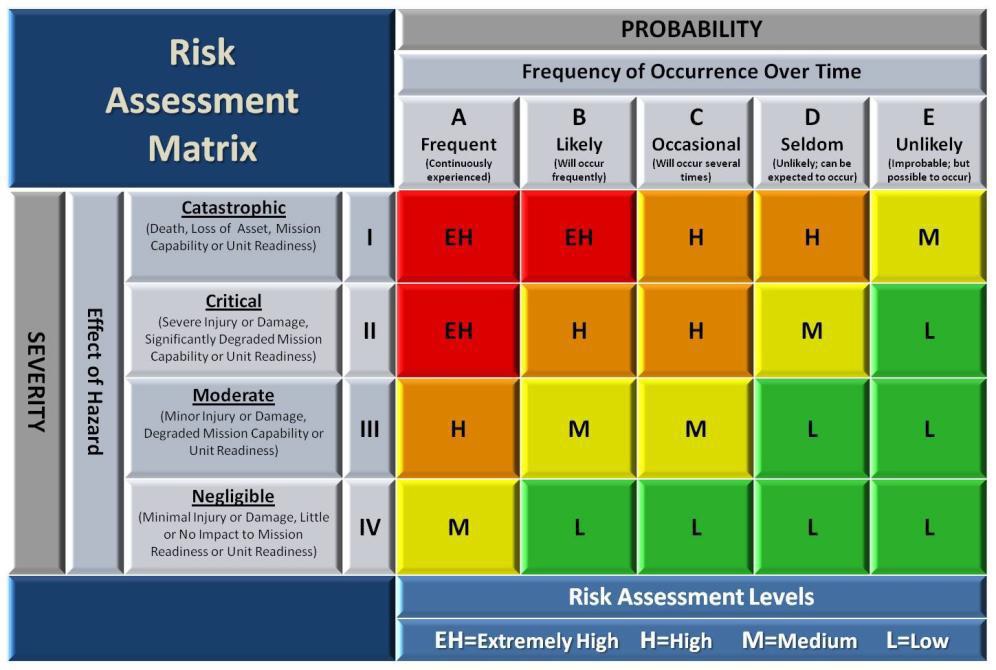
What Is The Primary Purpose Of Conducting Security Risk Assessment
Like traditional crime terrorism is a local issue and is a responsibility shared among federal state and local governments. Electrical Safety Risk Assessment Checklist.

Post Event Evaluation Report Template 3 Templates Example Templates Example In 2021 Report Template Evaluation Templates
The objective is to provide reasonable assurance that all business objectives will be met.

What is the primary purpose of conducting security risk assessment. The new policing model forContinue Reading. Electrical_Equipment_Risk_Assessment_v20-1doc 7917 downloads HSDG RA. One of the most popular approaches for conducting RCSA is to hold a workshop where the stakeholders identify and.
These tools could be used to cross-check or complement the analyses using the World Bank tools. All doctors should have an individual risk assessment in their workplace. However engagements with third parties do not end there or even after risk mitigation.
According to National Information Assurance Training and Education Center risk assessment in the IT field is. NIST SP 800-53A SAR Task 4-4 Conduct initial remedial actions on security controls based on the findings and recommendations of the SAR and reassess remediated controls as appropriate. All ecological risk assessment plans must.
Managers use the results of a risk assessment to develop security. Risk and control self assessment RCSA is a process through which operational risks and the effectiveness of controls are assessed and examined. This checklist is used to assist in conducting a risk assessment for hazardous substances and chemicals in the hairdressing nail and beauty industry.
If you were doing a PIA full form search you could be taken down a completely different path if you landed on Social Security PIA instead of PIA privacy. An assessment is a moment-in-time look into a vendors risks. The primary responsibilities of the SNP are as follows.
The Energy Sector Management Assistance Program ESMAP Hands-on Energy Adaptation Toolkit is a stakeholder-based semi-quantitative risk-assessment approach to prioritize hazards and risks to a countrys energy sector. We performed two types of risk assessment. The initial analysis of the risk posed to the financial sector which led to the creation of the use case and the desired security characteristics and an analysis to show users how to manage the cybersecurity risk to the components introduced by adoption of the solution.
Security Assessment Report SAR documenting the issues findings and recommendations for the security control assessment. Determine the scope and boundaries of the assessment. In the wake of September 11 local law enforcement has taken on a pivotal role in preventing and responding to future incidents of terrorism within the United States.
Ongoing vendor monitoring throughout the life of a third-party relationship is critical as is adapting when new issues arise. Ecological risk assessments also inform an environmental damage assessment in which loss of ecological services eg flood protection fishable waters will be valued monetarily. The tool also helps identify adaptation options.
The risk assessments purpose determines who participates in planning. Jose Docobo ABSTRACT. A study of the vulnerabilities threats likelihood loss or impact and theoretical effectiveness of security measures.
A Social Security PIA refers to the term primary insurance amount which is the amount of Social Security a person receives if they elect to get benefits at the standard retirement age. The BMA has called upon the NHS to introduce an effective system of risk assessment for all doctors including those from a BAME black Asian or minority ethnic background and ensure that doctors can work in a way that minimises risk to themselves and patients. To ensure appropriate robust processes exist in relation to the adherence to Lloyds Minimum Standards Issues raised by the Lloyds Oversight Manager or Lloyds oversight teams are addressed in a timely manner.

What S The Difference Risk Management Risk Assessment Risk Analysis
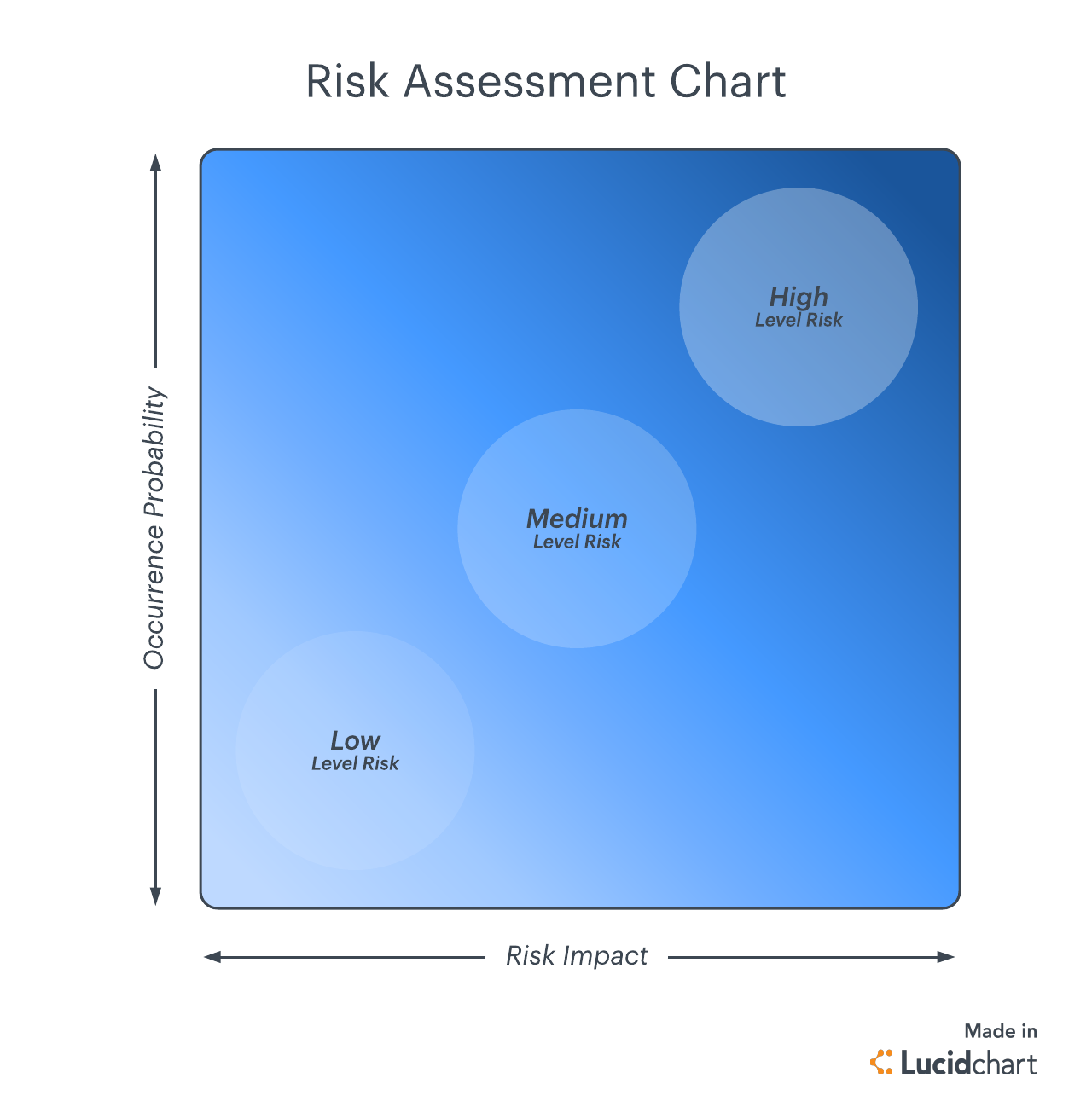
A Complete Guide To The Risk Assessment Process Lucidchart Blog

Security Risk Management An Overview Sciencedirect Topics

How To Perform It Security Risk Assessment

Security Risk Management An Overview Sciencedirect Topics

How To Perform It Security Risk Assessment

Research Report Template Report Template Research Report Templates

Explore Our Sample Of Cyber Security Incident Response Plan Template Cyber Security Online Business Plan Template Online Business Plan

5 Steps Of The Risk Management Process

Risk Impact Assessment And Prioritization The Mitre Corporation

The Hipaa Privacy Rule Checklist 2020 Hipaa Hipaa Compliance Checklist

What S The Difference Risk Management Risk Assessment Risk Analysis

5 Steps Of The Risk Management Process

Security Risk Assessment An Overview Sciencedirect Topics

Security Risk Management An Overview Sciencedirect Topics

Threat Modeling 12 Available Methods
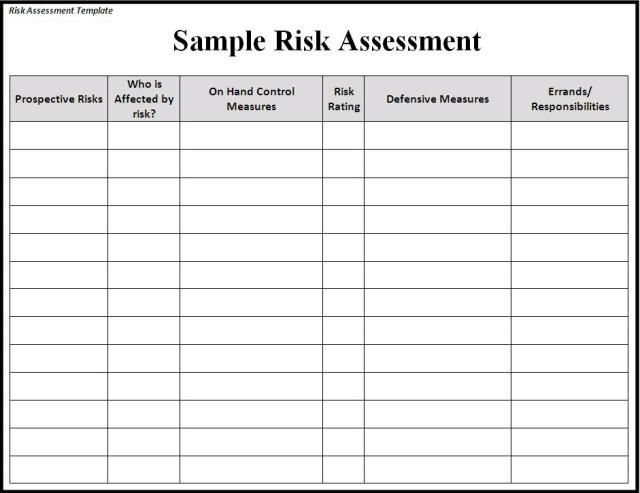
Crisis Mapping And Cybersecurity Part Ii Risk Assessment Risk Analysis Risk Management Assessment
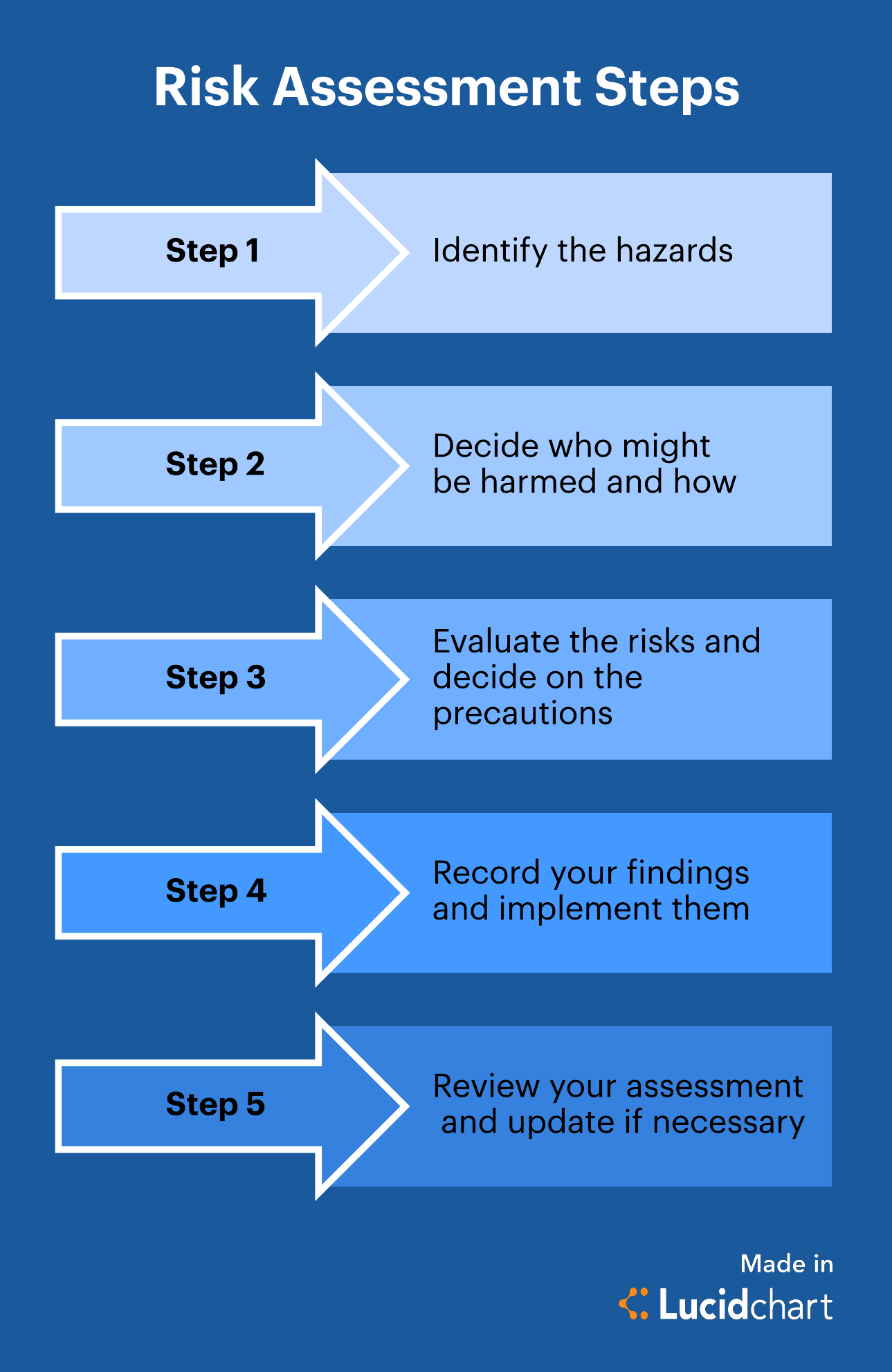
A Complete Guide To The Risk Assessment Process Lucidchart Blog